Political app vulnerabilities raise concern
Thursday, October 22, 2020

|
Doug Dooley |
A deeper analysis of the Trump and Biden app vulnerabilities reveal Official Trump 2020 App is nearly 3x as secure as the Vote Joe App on Android but on iOS they both scored bad.
With election season upon us, the US population is being inundated by candidate and proposition propaganda from a variety of sources – including television, the US mail, and mobile device apps. As annoying as this flood of information is at times, it’s important to understand that when it comes to these popular apps, and in fact all apps, if certain security measures and best practices are not architected in development, their use can bring about some serious consequences.It was reported in June and September that there were vulnerabilities in both the Official Trump 2020 and Vote Joe apps. As we learned most recently, vulnerabilities enabled Target Smart (an embedded third-party API service) to gather contact and voting information of more than 191 million voters and 58 million unregistered, voting age consumers. However, at Data Theorem we leveraged our AppSec solution rooted in a DevSecOps framework that automates API security analysis, vulnerability inspection and remediation to delve into the makeup of the Android and iOS versions of these apps, revealing some critical concerns.
Data Theorem used its Analyzer Engine, which leverages runtime analysis fully integrated into the CI/CD process to conduct continuous, automated security inspection, to investigate whether and to what extent Android and iOS data protection for these political apps has been employed using important security measures recommended by Google and Apple. As a result, the tool reported a security score which shows how secure each app is, and grades against the best practices that should be applied, but might not be.
How Trump and Biden app security checks did
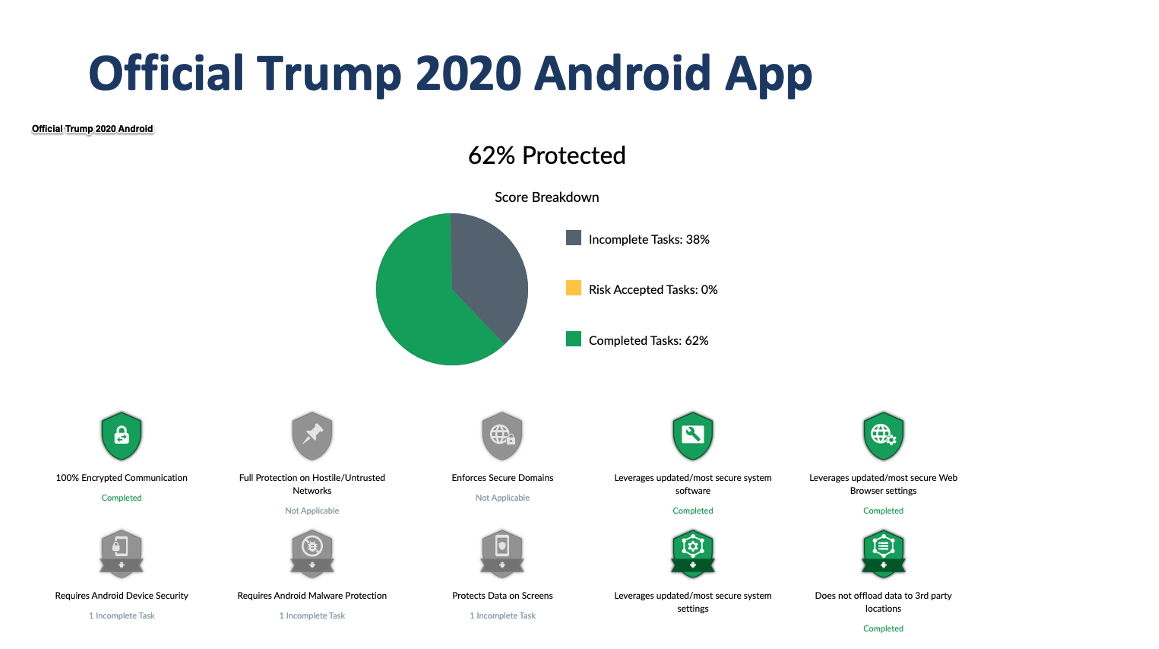
On the Android side, the Official Trump 2020 app is nearly three times as secure as the Vote Joe app. The Trump app posted a 62 percent protection score, while the Biden app earned a 22 percent protection score. One reason is because the Trump app leverages newer security and privacy features found in the most recent version of Android OS. For example, the app prevents any clear text traffic originating from the app. The Trump app also prevents any private data from being backed up.
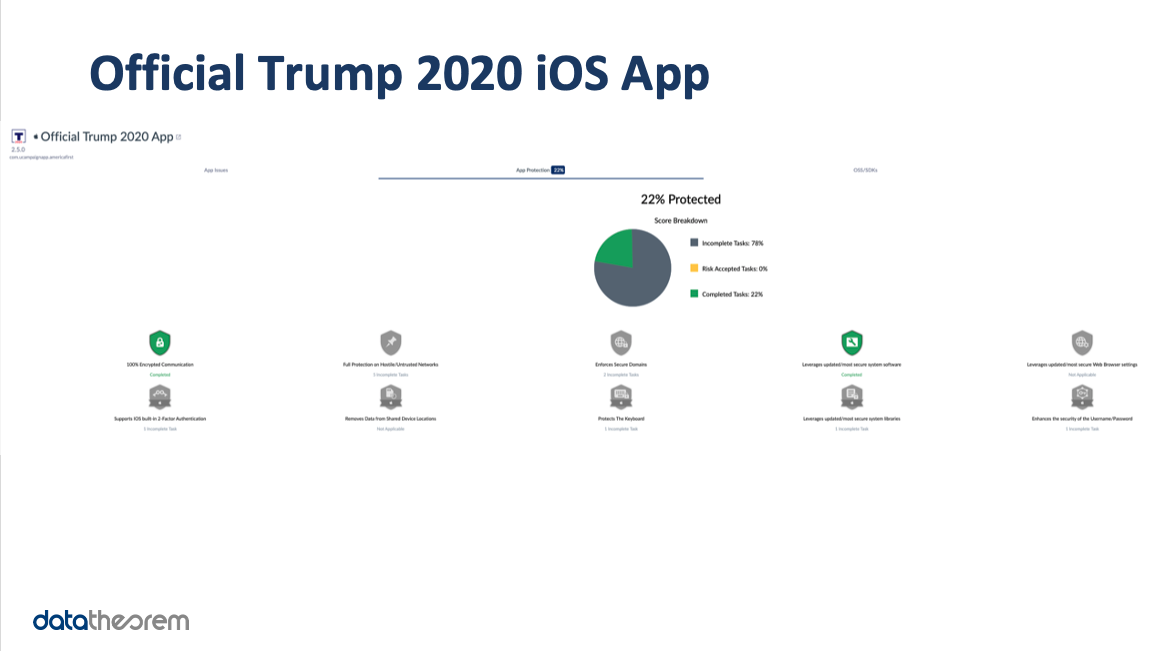
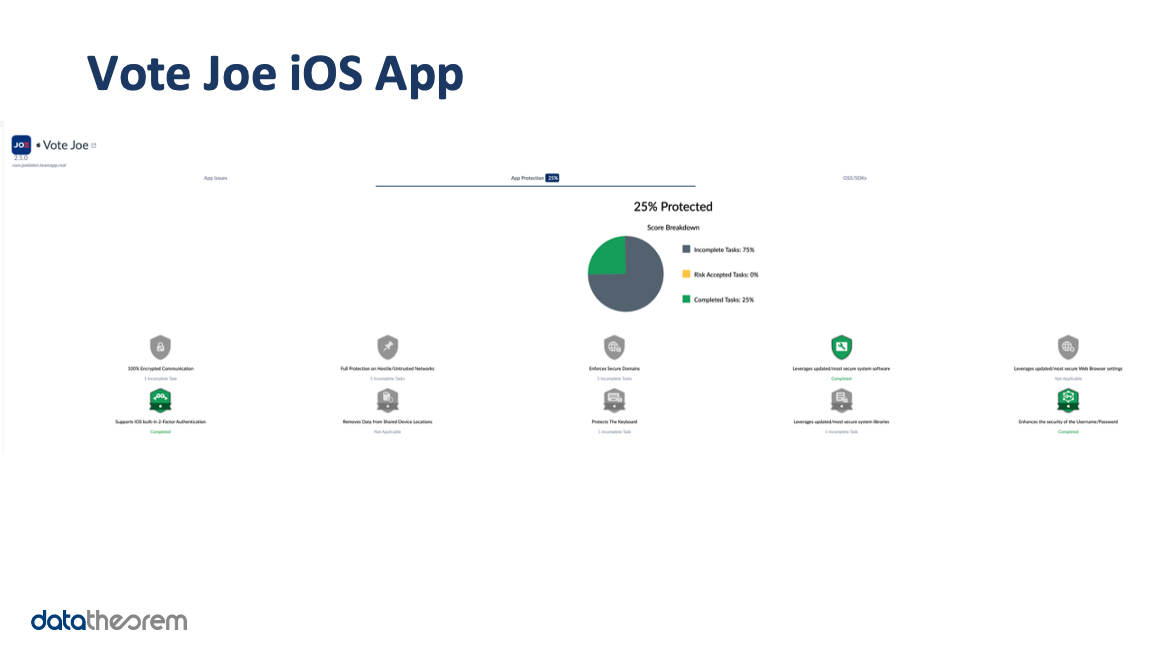
According to our analysis, both the Trump and Biden apps enable safe browsing to block any malicious domains from loading on the App’s WebView. However, neither apps enforce the “Verify Apps” feature, which scans for potentially harmful apps on the device.Considering the iOS versions of these apps, they scored nearly equally very low in our security protection analysis. The Vote Joe iOS app earned a 25 percent protection score, while the Official Trump 2020 iOS app posted a 22 percent protection score. On the plus side, both apps are using the latest SDKs. The Biden app utilizes APIs that improve the security of its authentication/sign-in flow, including automatic 2FA code entry and strong password generation/autofill. The Trump app is credited with using a “Strong App Transport” policy that guarantees all network requests are using https.

But with such low protection scores, you can imagine there is a plethora of areas where these iOS apps fall down in protecting users and data. For example, neither app has implemented SSL Certificate Pinning, an added safeguard against the app’s network requests being intercepted by a malicious party – aka Man-in-the-Middle (MiTM) attack. In addition, both apps use an unsafe Serialization API called NSCoding, an Objective-C protocol designed to allow serialization and deserialization of code objects making them vulnerable to object substitution attacks. And finally, both apps allow third-party keyboards to be used. Custom keyboards observe user input and can potentially record/export the collected data via keylogging.
Specific to the Biden iOS app, it has an App Transport Security policy that allows any non-https request to succeed. On the Trump side, the iOS app’s backend server, app.donaldjtrump.com, lacks OCSP stapling that can help protect end user privacy of their browsing history. Also, unlike the Biden app, the Trump app does not utilize APIs that improve the security of the authentication/sign-in flow.
There are a lot of security issues to be concerned about in these apps, but what does this all really mean to real end users?
When considering the Android version of these apps, many of the threat scenarios are the same when a malicious app is installed on the user’s device. I mentioned earlier that the apps do not enforce the “Verify Apps” feature. With the Verify Apps feature disabled, apps that are side-loaded on the user’s device are not scanned for malware. The apps are also not protecting users’ screens from other third-party apps installed on the device. If a user has installed a malicious app that spies on the user’s screen, the malicious app can record the user’s screen and send the recording to an untrusted server, eventually to be seen by an attacker.
Both apps are vulnerable to the Android Strandhogg issue, a vulnerability that affects almost all Android apps and allows malware to pose as legitimate apps, with users unaware they are being targeted. The only protection against this kind of attack is to make sure malicious apps are not installed on the device, which makes the Verify Apps feature even more critical.
Turning to the iOS side, the Vote Joe app has serious threat scenarios around accessing user/session data and impacting the behavior of the native app. For example, the app includes an SDK that does not check for path traversal characters when unarchiving a zip file, so a malicious zip file can overwrite local files. The app also does not enforce HTTPS connections, so if the above SDK were to fetch zipped resources insecurely, parties on the local network would be able to intercept them and send a malicious archive to the device.
With the iOS version of the Trump app, many of its security issues are not easily attackable because of protections put in place in other parts of the stack. For example, the app does not perform integrity checks on data that has been serialized to the filesystem like the Biden app, but with a strong “App Transport Security” policy in place, there are significantly reduced vectors for exploiting this issue in the Trump app. It does however load some content in a WebView without limiting that Webview’s access to APIs that can reveal which images a user pauses on, what content they copy/paste, and which sections of pages they reach while scrolling, putting the user’s privacy at risk.
Applications, especially mobile apps, can be informative, helpful, and fun. Increasingly, apps seem to be a necessary part of our daily lives. With a highly political climate, this upcoming election is likely to break records for early voter turnout and engagement using political apps. Yet the analysis of these presidential candidate apps shows how developers need to invest more in safeguarding features to protect their apps from data breaches. Security measures and best practices are well publicized by the platform providers to help secure users’ data and protect their privacy. But security teams working with developers need to prioritize and help architect these safeguards into their apps. The good news is that the number of DevSecOps tools are growing for both developers and security teams which in turn make it easier for everyone involved in publishing more security-hardened apps, whether it’s for political reasons or not.
This content is made possible by a guest author, or sponsor; it is not written by and does not necessarily reflect the views of App Developer Magazine's editorial staff.

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here